How to know the number of users on your network and also find out if your being hacked using CMD
17th Jun 2018 | category: Wired Networks | Hits: 1188
Command Prompt or CMD is one of the most powerful tools in Windows, but sadly, it is also the most ignored or least used tool by the Windows users unlike the Unix, Linus and Mac OSX users who make extensive use of the terminal windows which are referred to as the cmd in windows. With the advent of the GUI based operating System, users starting feeling that computing through the command based tools was boring and tiresome as took one to understand and memorize the command they used to accomplish their routine tasks. This ultimately led the command prompt or command line into obscurity. And it ended up being used by sophisticated people normal users referred to as nerds or geeks. However the cmd is not useless, in fact, it’s pretty useful. This article provides some excellent tricks and how to’s that will make you acknowledge the power of the Windows command line tool. It will also provide you with an insight of how the windows command line is not only a useful too but also a tool you should definitely give more respect to.
For someone to launch a hack, they either need to be on site or do it remotely but I all scenarios, the computer being hacked has to be on a network of some sort otherwise no hack will be possible. If you are on a private network, it is always wise of you to check for the number of users on the same network so as to know if any of them are not allowed to have access. To accomplish this using CMD,
Click “Start ” on your keyboard and then type “cmd” without the quotes into the quick search. Right click the app link and click “Run as administrator”, if prompted for a password enters the password or if the prompt requires a yes or no, select yes. A window just like the one below will pop up.
 Type "CMD"
Type "CMD"
In the window above, type “net view” without the quote s and hit enter. A list of the all the users on the same network as you will be generated and shown as below.
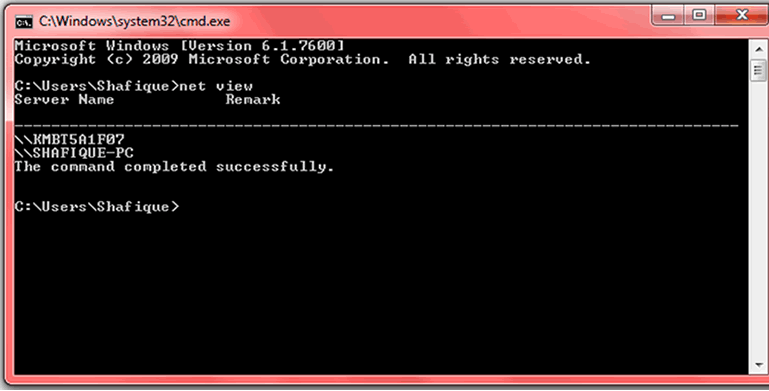 type “net view”
type “net view”
Currently the users on the network on which the command was run were two. Including the user on the computer running the command. If any suspicious user is listed it is easy to either forward their username to the network administrator so that their computer can be blocked from accessing the network or queried for verification of access rights to the network.
How to Tell If your computer is being hacked using CMD
Launch CMD as described above.
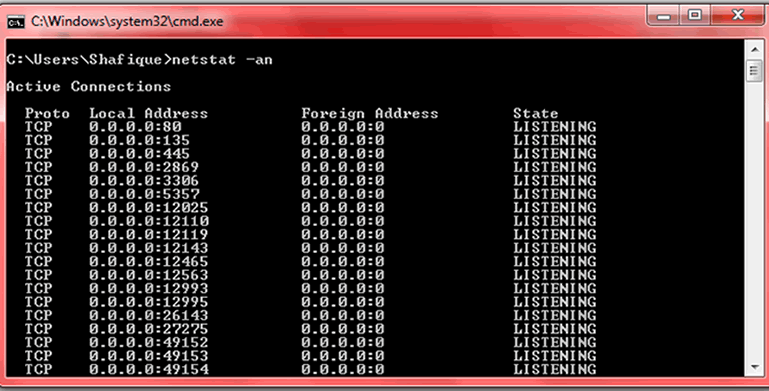
In the black screen, type “netstat -an” without the quotes and hit the enter key on your keyboard. The wait for a few seconds for the command to complete running.
 Launch CMD
Launch CMD
The above command calls for a network statics. Look through the result of the command. The first column the type of connection which in this case is both TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). The second column shows you the local address, third the foreign address and finally the last column shows the status of the connection.
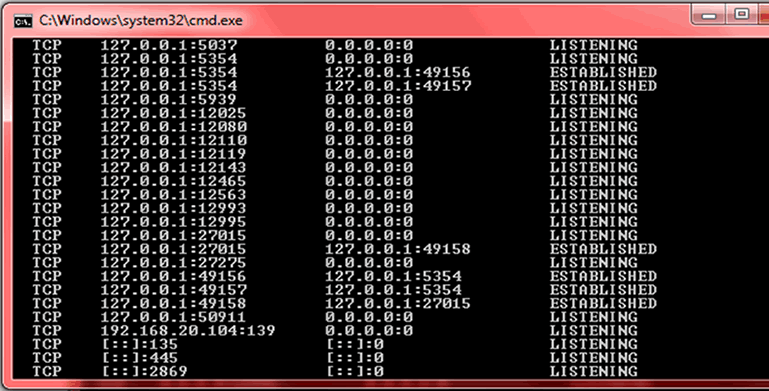 List View
List View
Carefully check the port numbers for an intrusion. The port numbers follow the IP or server address in the following format: “xxxxxx”, Ports between 0 and 1023are normally safe, ports between 1024 and 49151 are relatively safe too, and you should put focus and attention on ports between 49152 and 65535. Most P2P software applications use the final port range, so close any P2P applications which may be running and run the command again.
Check the suspicious IP addresses by looking at third column. The foreign addresses refer to the location of the connection destination. Use a search engine like google, bing or duck duck go to search through these IP addresses to see if they match up with programs such as Windows LIVE Messenger, Skype or Facebook Messenger or any other program you may be running.
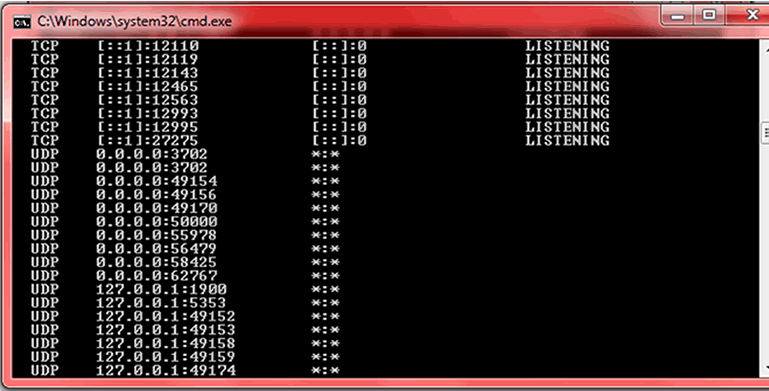 Check the suspicious IP
Check the suspicious IP
If they don’t match any program, they its safe to say and conclude that you have an intruder hacking your computer.
To remedy the hack in a fast and robust way, run the following commands in you CMD.
Ipconfig /release, this command will release your current computer’s ip address,
Ipconfig /renew, this command will automatically assign your computer a new ip addresses hence releasing the initial ip address through which the hacker was accessing your computer to perform the hack.